Table of Contents
- Understanding DDoS Attacks
- Grabify Tools and Their Impact
- What is a Stresser?
- Layer 7 Stress Testing
- IP Spoofing and Layer 4 Attacks
- Protecting Against DDoS
Understanding DDoS Attacks
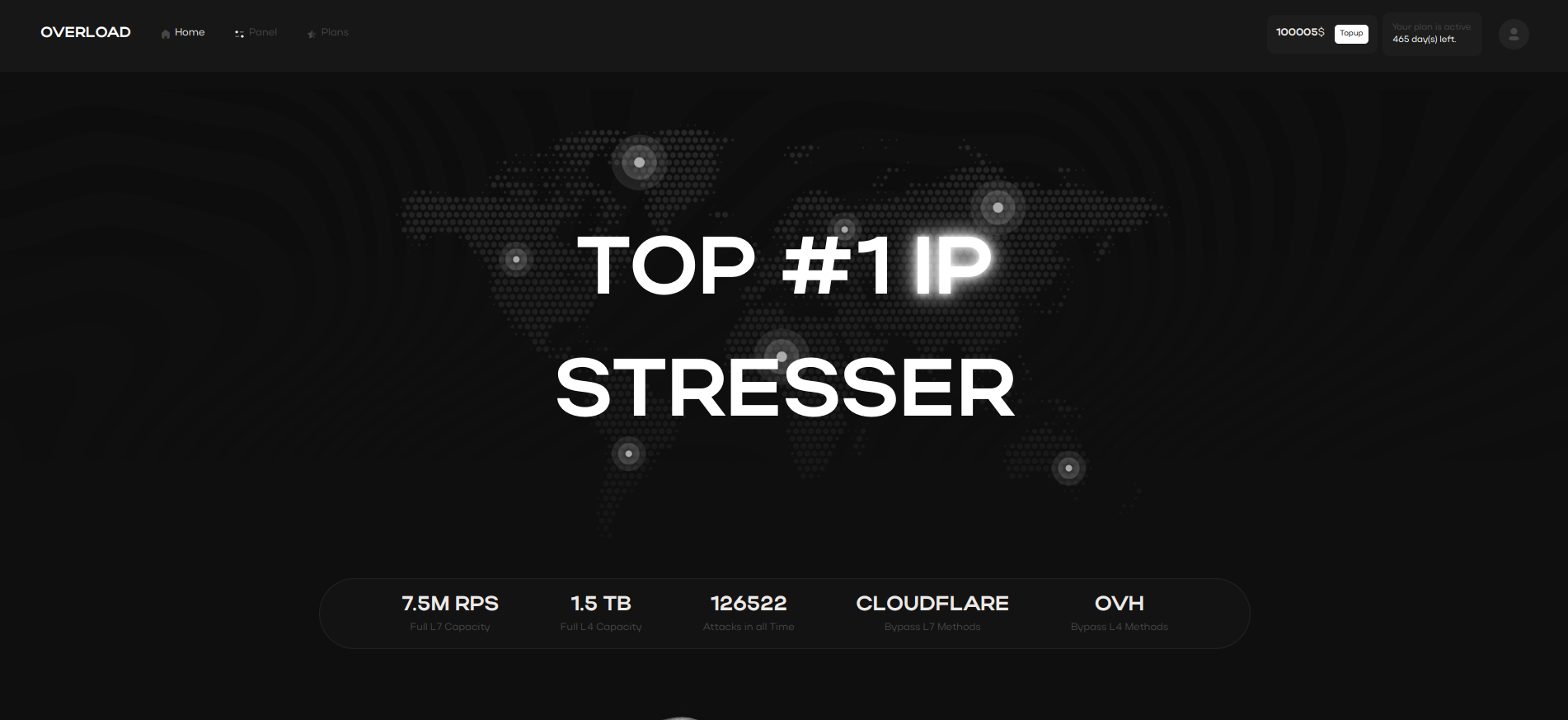
Distributed Denial of Service (DDoS) attacks flood networks with excessive requests, crippling services.
By analyzing their patterns, organizations can deploy proactive defenses and safeguard their critical infrastructure.
Grabify Tools and Their Impact

Grabify tools are designed to monitor and analyze traffic patterns.
They support cybersecurity measures by identifying potential threats and aiding in incident prevention.
What is a Stresser?

By simulating large traffic volumes and intense load conditions,
stressers aid in preventive cybersecurity. They are an integral part of modern
cyber resilience strategies, providing a realistic view of how infrastructure responds under peak load.
Layer 7 Stress Testing
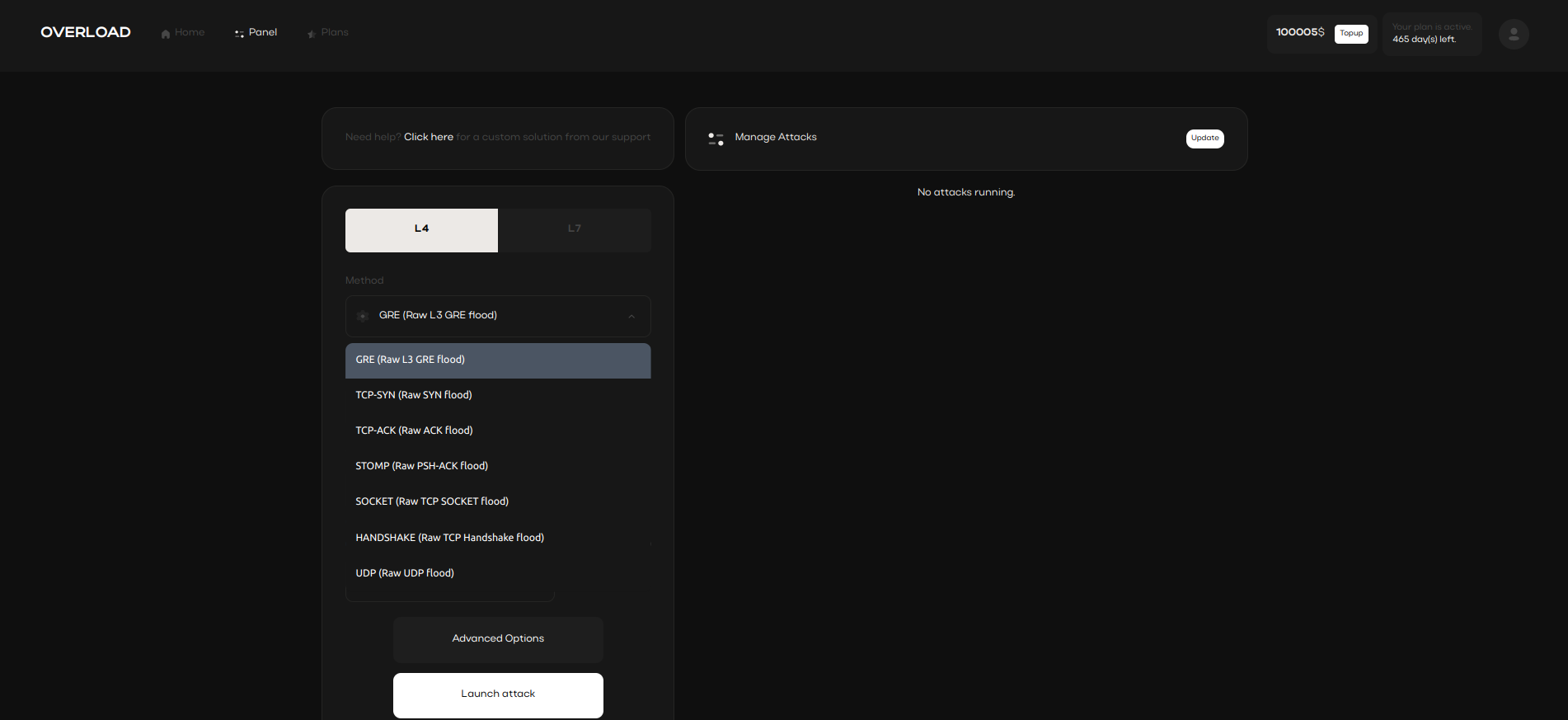
Layer 7 tools analyze application behavior under stress, providing insights into scalability
and enhancing user experience.
IP Spoofing and Layer 4 Attacks

Stresser tools with IP spoofing capabilities obscure the attacker’s identity,
preventing detection and enabling secure, concealed testing. IP spoofing aids in masking attack origins,
adding a layer of anonymity during cyber evaluations.
Protecting Against DDoS

DDoS mitigation strategies focus on identifying attack patterns and implementing traffic controls
to prevent system overload.